| Applies to:
PcVue 15 onwards |
||
|
|
||
| Summary:
Embedding SQL scripting in PcVue is extremely powerful, but this feature can be exploited to perform a malicious act, erase data, read sensitive data or even corrupt a system. But fortunately PcVue is equipped with tools to prevent these risks. This article is here to help you configuring your SQL queries safely within PcVue. |
||
|
|
||
| Details:
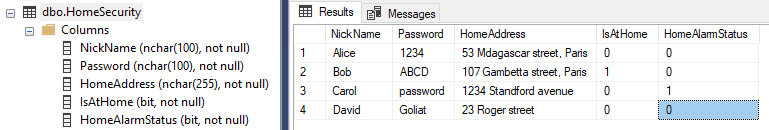
It is possible to modify queries dynamically using parameters. This is interesting in many situations but it can be dangerous too. Parameters are configured by default to be safely used but we will see that sometime we can improve security and why we should do it. Let us imagine we have this basic table in a database to retrieve personal information of different users:
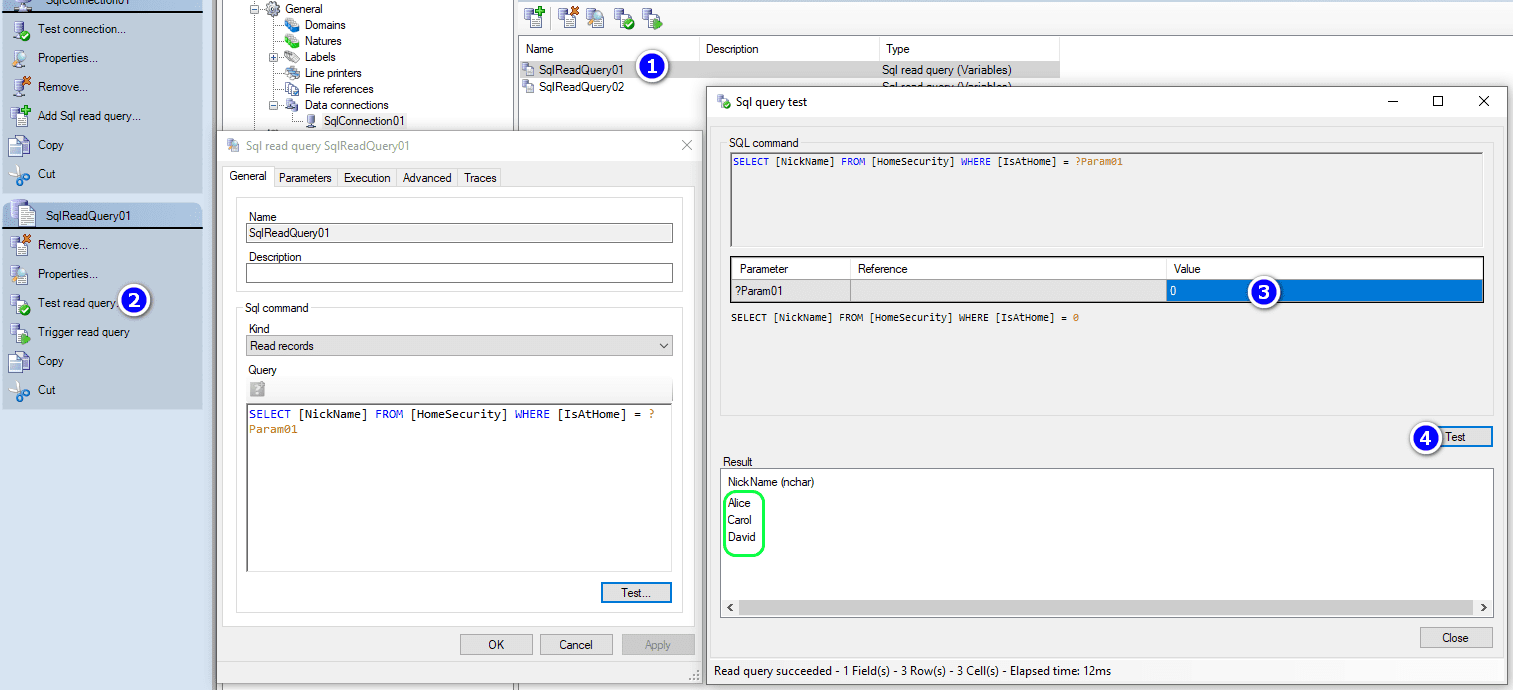
Sample 1We can prepare a query in PcVue in order to know who is at home or not: SELECT [NickName] FROM [HomeSecurity] WHERE [IsAtHome] = ?Param01 Normal usage will be to execute this query with ?Param01 at 0 to know who is at home or not:
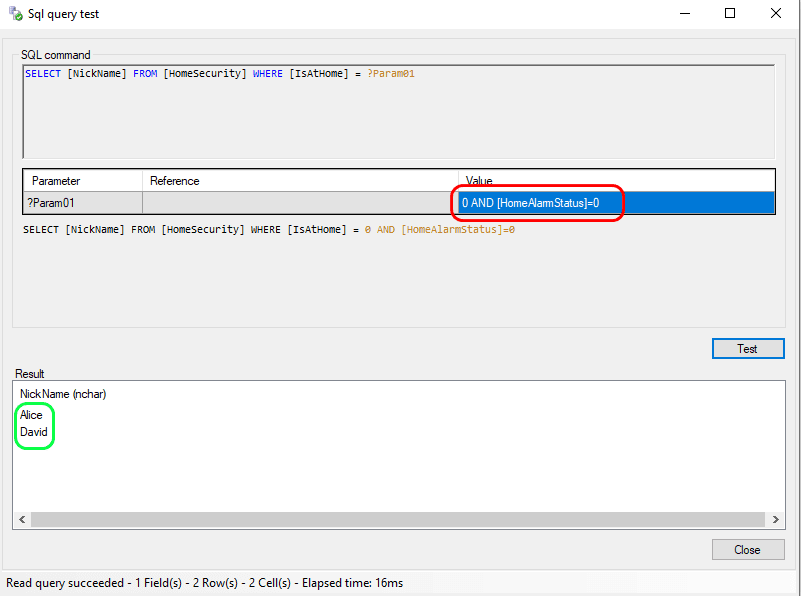
But a malicious user could retrieve sensible information like the fact that Alice and David are away and their alarms are not activated:
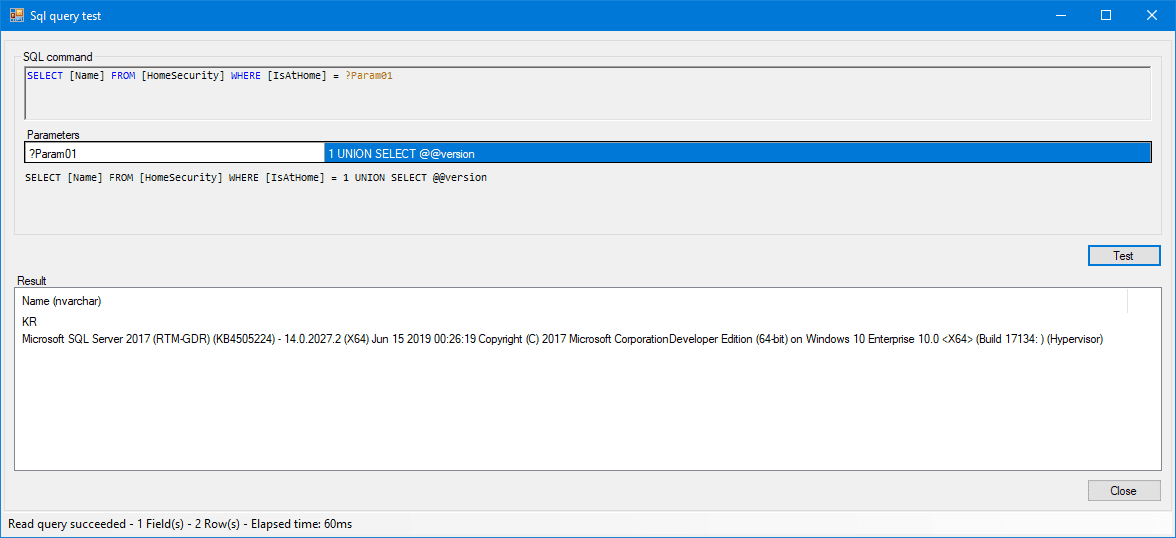
Another example of injection is to call a system variable to get SGBD version to exploit a vulnerability of the system.
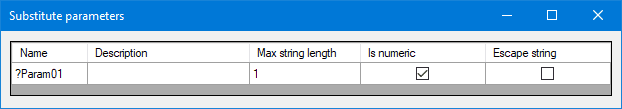
How to avoid these situations? Configure ?Param01 parameter in query configuration to limit the use of numerical value and limit the string length.
It will then not be possible anymore to use AND or OR magic keywords. It is also a good habit to limit the number of characters (max string lengh) to avoid a buffer overflow. |
||
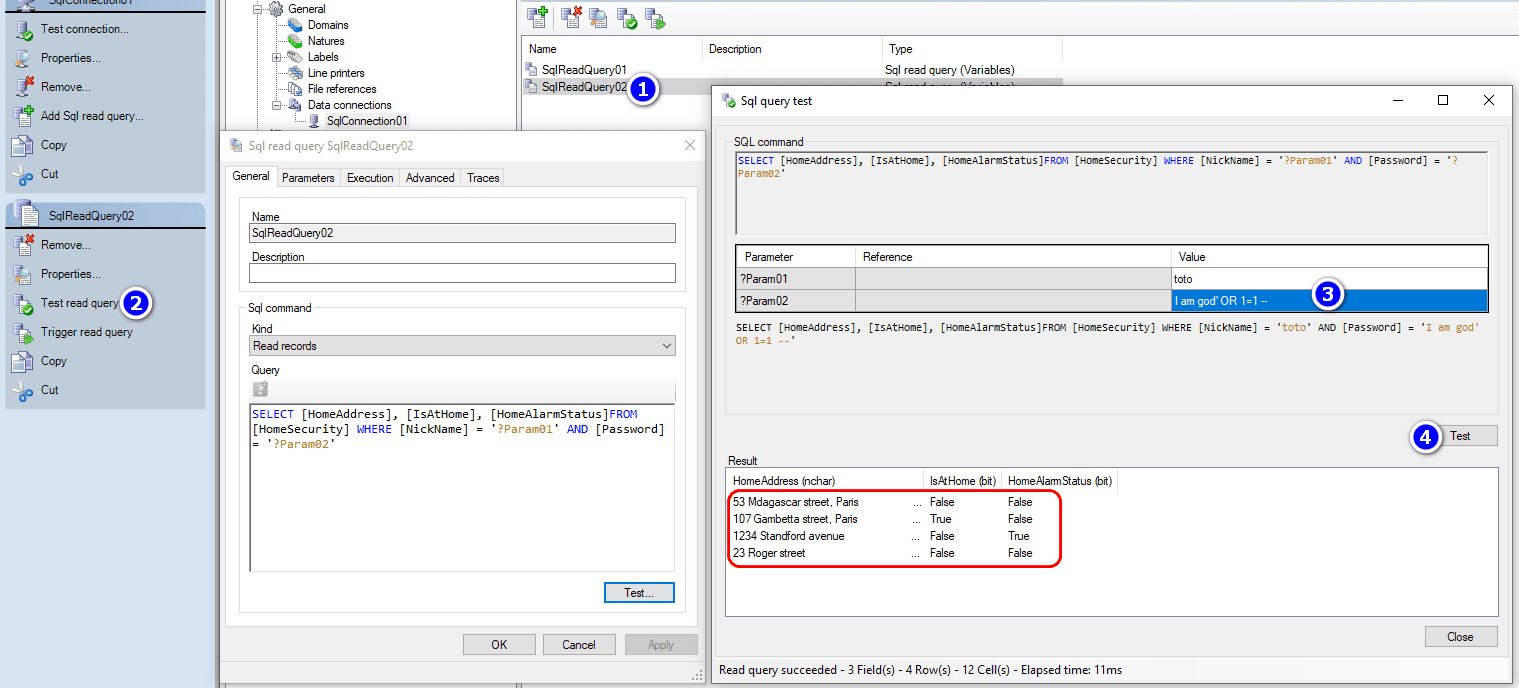
Sample 2We can also prepare the following query to retrieve user information if login and password match SELECT [HomeAddress], [IsAtHome], [HomeAlarmStatus]FROM [HomeSecurity] WHERE [Name] = ‘?Param01’ AND [Password] = ‘?Param02’ ?Param01 should only contain login ?Param02 should only contain password But if ?Param02 “Escape string” property is unticked, it will be easy for a malicious user to know all adresses interesting to visit or not, without knowing a login nor a password:
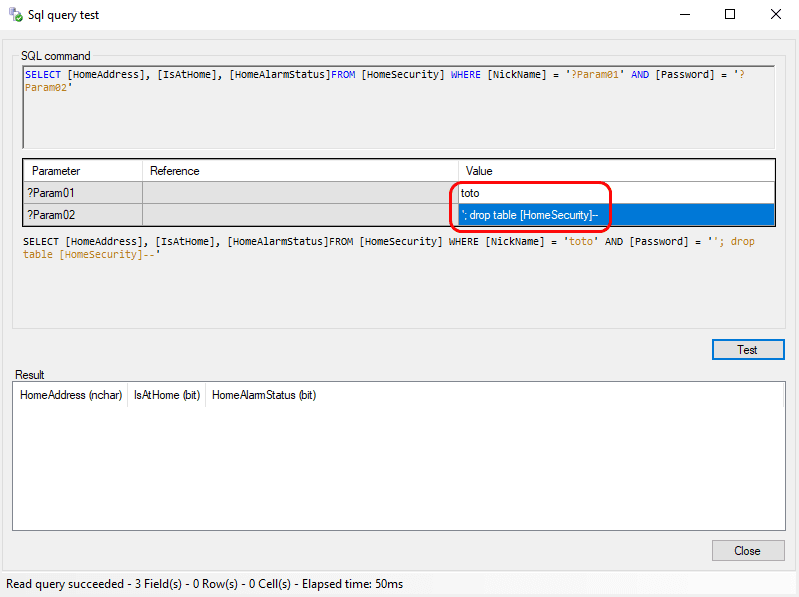
Here below, another example of injection to corrupt the system, here it will delete the [HomSecurity] table:
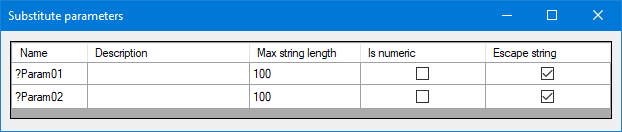
How to avoid these situations? Let the escape string option selected to escape malicious characters (by default activated), and define adequat Max string length.
Summary of the different options available in the parameters configuration
Truncate the parameter value substitution string. Ex: if value is 4 and parameter resolution is “My name” Result is “My n”
This option allows to verify if text value represents a numerical value or not
This option allows to escape the following characters:
|
||
|
|
Created on: 12 Jan 2021 Last update: 04 Sep 2024